[ad_1]
It supplies an progressive and user-friendly method to rework the expertise of customers with on-line providers and options. The solutions to “Is Web3 susceptible?” draw the limelight in direction of the benefits it brings to the tech panorama. There isn’t any method to deny that Web3 has the potential to rework on-line experiences with decentralization and thru empowering customers.
Then again, Web3 safety dangers have additionally been rising by way of their financial affect. Apparently, greater than 167 main assaults within the area of Web3 in 2022 resulted in approximate losses of virtually $3.6 billion. Inside the first half of 2022, Web3 safety hacks resulted in losses price over $2 billion, which is greater than all losses in 2021. Due to this fact, consciousness concerning essential vulnerabilities in Web3 safety is a necessary requirement for Web3 builders and founders. The next put up supplies you with a quick information to challenges with distinguished Web3 vulnerabilities and their options.

Fundamentals of Web3
Web3 is an progressive transformation within the primary construction of the online with new options primarily based on blockchain know-how. Specialists describe Web3 because the decentralized web, which might be developed over decentralized blockchains utilized in cryptocurrency networks, equivalent to Ether and Bitcoin.
The kind of vulnerability in Web3 is likely one of the distinguished issues, contemplating the truth that web sites and apps in Web3 can handle information in intuitive methods, similar to people. As well as, Web3 wouldn’t depend on blockchain know-how solely. The opposite applied sciences related to Web3 embody machine studying, distributed ledger know-how or DLT, and massive information.
Web3 envisions an open, clever, and autonomous web. One of many important highlights in favor of Web3 factors to the peace of mind of consumer management. Web3 ensures customers have full management over their information, digital belongings, and digital identities.
Need to change into a Cryptocurrency knowledgeable? Enroll Now in Cryptocurrency Fundamentals Course
Why Do You Have to Know the Web3 Vulnerabilities?
The necessity for studying about Web3 vulnerabilities has been gaining distinguished ranges of consideration in latest instances. Frequent responses to ‘what’s a vulnerability in safety’ would discuss with potential areas of assault. Within the case of Web3, the distinguished highlights deal with the enhancements launched by Web3. Then again, it is very important perceive how Web3 supplies safety. On the similar time, you also needs to deal with studying in regards to the notable safety threats which haven’t been addressed within the current Web3 structure.
Developments within the Web3 area are repeatedly increasing, particularly within the case of metaverse and NFT collections. Nevertheless, it’s also vital to surprise how Web3 presents higher safety than Web3. The doubts concerning kinds of safety vulnerabilities in Web3 emerge from the threats to Web3 tasks.
For instance, an assault on the Wormhole Bridge resulted in losses price over $360 million. Apparently, a hacker had exploited a vulnerability within the design of the sensible contract operate of the bridge to the Solana blockchain. Due to this fact, consciousness concerning Web3 vulnerabilities is a necessary requirement for enhancing belief within the Web3 ecosystem.

What are Web3 Vulnerabilities?
Earlier than figuring out probably the most noticeable vulnerabilities in Web3 tasks, you have to perceive the definition of vulnerabilities. The issue with vulnerability in cyber safety for Web3 options is the sophisticated nature of vulnerabilities. Web3 tasks have led to an unprecedented rise within the variety of safety points. The largest drawback in making certain Web3 safety focuses on the problem of acquiring the assistance of specialists. Whereas bug bounty applications serve efficient leads to the identification of Web3 vulnerabilities, many cybersecurity professionals dismiss Web3 and blockchain as scams.
Web3 vulnerabilities are regularly changing into troublesome issues for Web3 tasks. The variety of Web3 purposes primarily based on blockchain know-how continues to rise and will increase the floor space for hackers. As a matter of truth, Web3 safety dangers characteristic similarities to standard cybersecurity points. Permissionless environments and prospects of bugs in sensible contract code current favorable components for compromises in sensible contract functionalities. Due to this fact, it is very important evaluate probably the most impactful Web3 vulnerabilities, their challenges, and the related options.
Construct your identification as an authorized blockchain knowledgeable with 101 Blockchains’ Blockchain Certifications designed to offer enhanced profession prospects.
Most In style Web3 Vulnerabilities
An in depth understanding of responses to ‘what’s a vulnerability in cyber safety’ would enable you to determine the standard issues for cybersecurity. Then again, the potential similarities between Web3 vulnerabilities and conventional safety dangers present higher flexibility for understanding the safety dangers in Web3. Right here is an overview of probably the most distinguished Web3 vulnerabilities you need to be careful for in 2023.
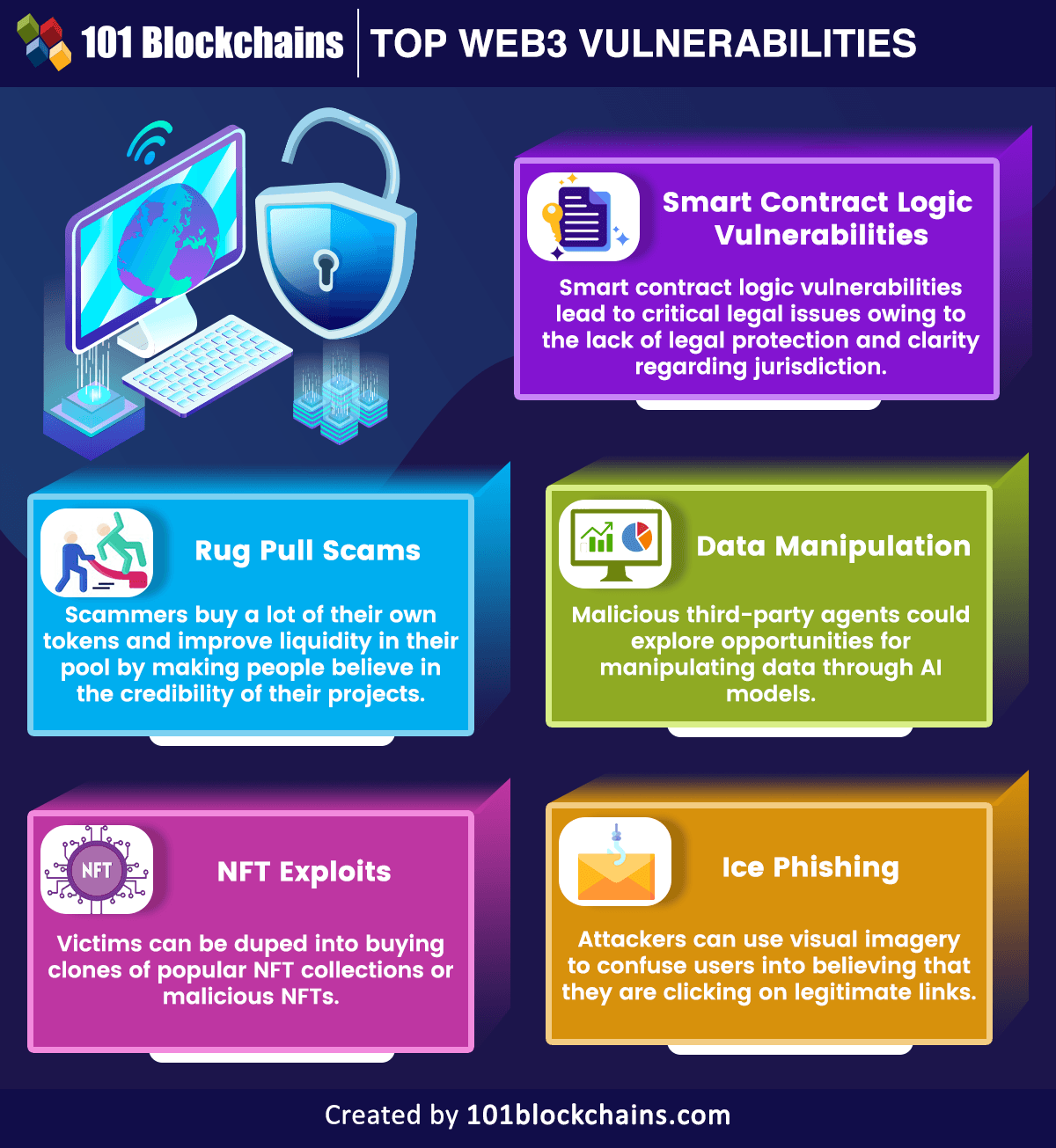
Please embody attribution to 101blockchains.com with this graphic. <a href=”https://101blockchains.com/blockchain-infographics/”> <img src=”https://101blockchains.com/wp-content/uploads/2023/04/High-Web3-Vulnerabilities-1.png” alt=”High Web3 Vulnerabilities=”0′ /> </a>
Curious to develop an in-depth understanding of web3 software structure? Be part of Yearly/Yearly+ Plan and Enroll Now in Web3 Software Growth Course!
Sensible Contract Logic Vulnerabilities
The use circumstances of sensible contracts in Web3 have opened up the roads for creating many progressive purposes. On the similar time, sensible contracts have emerged as one of many high Web3 vulnerabilities owing to faults within the software logic. Sensible contracts outline the specs of an settlement in a contract with code and work in keeping with the outlined logic.
Challenges with Sensible Contracts
The issue with sensible contracts is that they must be deployed on a blockchain community for desired operations. The presence of sensible contracts on decentralized blockchain networks implies that the safety of sensible contract information relies on the safety of the underlying blockchain.
The kinds of safety vulnerabilities in sensible contracts emerge from the problems within the logic of the sensible contracts. Logic hacks on sensible contracts have been carried out for exploiting varied options and providers in Web3 tasks. On high of it, sensible contract logic vulnerabilities may also result in essential authorized points owing to the shortage of authorized safety and readability concerning jurisdiction.
Options for Sensible Contract Vulnerabilities
The options for addressing vulnerabilities with sensible contracts would revolve round cautious analysis of the character of blockchain and sensible contracts. Cautious analysis of the blockchain and sensible contracts all through completely different phases, from planning to the testing section, may help in reviewing all blockchain traits. You possibly can handle sensible contract vulnerabilities and the related Web3 safety dangers by studying about blockchain and sensible contract programming.
Curious to know the whole sensible contract growth lifecycle? Be part of Yearly/Yearly+ Plan and get free entry to the Sensible Contracts Growth Course Now!
Rug Pull Scams
One other distinguished addition amongst vulnerabilities within the Web3 panorama refers to rug pull scams. Rug pulls scams discuss with occasions during which malicious Web3 builders abandon a venture after having access to huge chunks of investor wealth. The definition of rug pull vulnerability in cyber safety is just like Ponzi schemes in the true world. A gaggle of builders created a Web3 venture and a local token that’s listed on decentralized exchanges in pair with well-liked cryptocurrencies equivalent to Ethereum.
Challenges with Rug Pull Scams
Probably the most distinguished problem with rug pull scams is the truth that you don’t get a whiff of foul play earlier than it’s late. Rug pulls scammers to start out by creating hype round their venture on Twitter, Telegram, and completely different social media platforms. Some rug-pull scams additionally rent influencers to make folks imagine within the credibility of the venture.
As well as, the scammers purchase lots of their very own tokens and enhance liquidity of their pool, thereby incomes the religion of traders. The issue with such a kind of vulnerability in Web3 turns into extra sophisticated with the convenience of itemizing tokens with none prices on decentralized exchanges.
Options for Rug Pull Scams
The really useful resolution for avoiding losses attributable to rug pull scams is due diligence. You should make investments efforts in complete analysis a few Web3 venture earlier than investing your cash in it. Ranging from the token pool to the main points of the founders and roadmap of the venture, you have to evaluate completely different features of Web3 tasks to keep away from the dangers of rug pull scams.
Excited to be taught the essential and superior ideas of ethereum know-how? Enroll Now in The Full Ethereum Know-how Course
NFT Exploits
NFTs or non-fungible tokens are additionally different widespread targets of Web3 safety threats. Non-fungible tokens play a vital function in driving the mainstream adoption of cryptocurrencies and inspiring the acceptance of Web3. NFTs can serve a number of use circumstances aside from defining distinctive proofs of asset possession.
Challenges with NFT Safety
The responses to “Is Web3 susceptible?” with respect to NFTs would additionally deal with sensible contracts, which outline the possession document of NFTs. Non-fungible tokens are a relatively new know-how, thereby implying the need for familiarizing themselves with challenges to their safety. For instance, victims might be duped into shopping for clones of well-liked NFT collections or malicious NFTs. Just one click on on a hyperlink for a malicious NFT can grant full entry to your NFT assortment or crypto belongings.
Options for NFT Safety
The identification of vulnerability in cyber safety for non-fungible tokens doesn’t recommend that you shouldn’t use NFTs. Quite the opposite, you have to search for higher options that may enable you to develop a complete understanding of vulnerabilities in NFT sensible contracts. Moreover, you too can leverage alerts and notifications for suspicious actions in NFT marketplaces to keep away from safety dangers.

Information Manipulation
One other distinguished concern in Web3 safety factors to the chances of knowledge manipulation in dApps, that are an important element of the Web3 panorama. Decentralized purposes depend on peer-to-peer networks and distributed codebase, which helps in storing information.
Challenges of Information Manipulation
AI is likely one of the very important applied sciences within the Web3 panorama, and you could find many dApps and sensible contracts utilizing synthetic intelligence. The AI fashions want massive quantities of high-quality information for coaching on a specific matter. With out ample safeguards for dApps or sensible contracts, malicious third-party brokers may discover alternatives for manipulating information by way of AI fashions.
Resolution for Information Manipulation
The options for Web3 safety dangers with information manipulation level on the choice of safe blockchains for deploying dApps.
Construct your fluency in Web3 and develop decentralized options with the world’s first Web3 Skilled Profession Path with high quality sources tailor-made by trade specialists Now!
Ice Phishing
The record of distinguished Web3 safety vulnerabilities additionally contains ice phishing as a latest addition. It focuses on the usage of misleading methods for duping customers into signing malicious transactions, which grant permissions to the attackers to make the most of the consumer’s tokens. The origins of ice phishing emerge from the ability of delegation of token utilization permissions.
Challenges in Ice Phishing
Ice Phishing methods are one of the harmful kinds of safety vulnerabilities in Web3 as they deal with social engineering assaults. Attackers can use visible imagery to confuse customers into believing that they’re clicking on legit hyperlinks.
Options to Ice Phishing
The answer to ice phishing factors to the need of safety coaching. Web3 customers should comply with the perfect practices for interacting with emails and double-check earlier than clicking on hyperlinks. It is best to take note of the logos, web site URL, and venture identify fastidiously to keep away from problems with ice phishing.
Be taught the basics, challenges and use circumstances of Web3.0 blockchain from the E-book: AN INTRODUCTION TO WEB 3.0 BLOCKCHAIN
Conclusion
The define of the notable vulnerabilities in Web3 proves that Web3 just isn’t as safe as everybody imagined. It’s a new technological idea and has its fair proportion of setbacks in safety. Most vital of all, the high Web3 vulnerabilities deal with figuring out areas of assault that may generate handy outcomes for attackers. For instance, a easy error within the sensible contract code can result in losses of hundreds of thousands of {dollars}. Due to this fact, analysis on Web3 vulnerabilities could be an important requirement for supporting the adoption of Web3 sooner or later.

*Disclaimer: The article shouldn’t be taken as, and isn’t supposed to offer any funding recommendation. Claims made on this article don’t represent funding recommendation and shouldn’t be taken as such. 101 Blockchains shall not be answerable for any loss sustained by any one who depends on this text. Do your personal analysis!
[ad_2]
Source link



